Lost your password? Please enter your email address. You will receive a link and will create a new password via email.
Please briefly explain why you feel this question should be reported.
Please briefly explain why you feel this answer should be reported.
Please briefly explain why you feel this user should be reported.
7.b) A negative feedback amplifier has the following parameters:
g
g
See less1(i). The Von-Neumann bottleneck is a problem, which occurs due to
speed disparity between CPU and main memory
speed disparity between CPU and main memory
See less1.(i) What is the output of this C code ?
ans:- (c) 3.000000
ans:- (c) 3.000000
See less1(iii). The general solution of p = log ( px – y), Where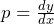 , is
, is
Ans:- $y=cx - e^c$ Explanation:- p = log(px - y) $\Rightarrow px - y = e^p$ $\Rightarrow y = px - e^p$ $\Rightarrow p = p.1 + x\frac{dp}{dx} -e^p\frac{dp}{dx}$ $\Rightarrow (x-e^p)\frac{dp}{dx} = 0$ $\Rightarrow$ p = c or $x = e^p$ $\therefore$ general solution $y = cx - e^c$
Ans:-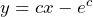
Explanation:-
p = log(px – y)
 general solution
general solution 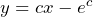
See less1(iv) In Fraunhofer diffraction the incident wavefront is
a) Plane
a) Plane
See less1(xv). The number of possible arrangements of two fermions in three cells is
c) 3 Explanation: All possible ways of arranging n particles in g phase cells According to Fermions: Number of ways of all possible arrangement = $\frac{g!}{n!(g-n)!}$ here g = 3 and n = 2 So, Number of ways of all possible arrangement = $\frac{3!}{2!(3-2)!}$ = 3
c) 3
Explanation:
All possible ways of arranging n particles in g phase cells
According to Fermions:
Number of ways of all possible arrangement =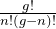
here g = 3 and n = 2 So,
Number of ways of all possible arrangement =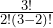 = 3
= 3
See less1(iv). The locus of the centre of curvature is called
b) evolute Explanation: In the differential geometry of curves, the evolute of a curve is the locus of all its centers of curvature. That is to say that when the center of curvature of each point on a curve is drawn, the resultant shape will be the evolute of that curve.
b) evolute
Explanation:
In the differential geometry of curves, the evolute of a curve is the locus of all its centers of curvature. That is to say that when the center of curvature of each point on a curve is drawn, the resultant shape will be the evolute of that curve.
See less8.(c) Given the following, determine the size of the sub fields ( in bits ) in the address for Direct Mapping, associative and Set associative mapping cache schemes :
Mile to batana
Mile to batana
See less20. By using the concept of equation of a line, prove that the three points (3, 0), (– 2, – 2) and (8, 2) are collinear.
To prove that the three points (3, 0), (-2, -2), and (8, 2) are collinear, that means these three points lie on the same line. Here we need to check whether (8, 2) satisfy the equation made by the point (3, 0) and (-2, -2) or not. We know that equation of the line passing through $(x_1, y_1)$ and $(Read more
To prove that the three points (3, 0), (-2, -2), and (8, 2) are collinear, that means these three points lie on the same line.
Here we need to check whether (8, 2) satisfy the equation made by the point (3, 0) and (-2, -2) or not.
We know that equation of the line passing through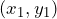 and
and 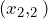 is
is
So, the equation of the line passing through (3, 0) and (-2, -2) is
5y = 2x – 6
2x – 5y – 6 = 0
Since the three points lie on the same line, then point (8, 2) must satisfy the equation 2x – 5y – 6 = 0
putting x = 8 and y = 2 in the above equation
2(8) – 5(2) -6 = 0
16 – 10 – 6 = 0
0 = 0
Which is true
Hence (3, 0), (-2, -2), and (8, 2) are collinear
See less1(iv). In order to execute a program instructions must be transferred from memory along a bus to the CPU. If the bus has 8 data lines, at most one 8 bit byte can be transferred at a time. How many memory accesses would be needed in this case to transfer a 32 bit instruction from memory to the CPU?
Prove that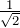 irrational
irrational

See lessProve that √5 is irrational.
Please click on below for answer. exercise 1.3.1
Please click on below for answer.
exercise 1.3.1
See lessCompare the focus of traditional relational systems with the focus of NOSQL systems?
Traditional relational systems • centralized data storage • structured data storage • data consistency / ACID compliance(a transaction must be atomic, consistent, isolated, and durable) • aggregation • powerful query languages NOSQL systems • distributed data storage • flexible data storage • schema-Read more
Traditional relational systems
• centralized data storage
• structured data storage
• data consistency / ACID compliance(a transaction must be atomic, consistent, isolated, and durable)
• aggregation
• powerful query languages
NOSQL systems
• distributed data storage
• flexible data storage
• schema-less data sets that include structured and semistructured data
• scalability
• high performance (at scale)
• availability through replication
See lessDiscuss the different techniques for executing an equijoin of two files located at different sites. What main factors affect the cost of data transfer?
Technique 1: Transfer second table (from 2nd site) to 2nd table (first site) and join them, then transfer the result of join into site 3 Technique 2: Transfer 1st table (from 1st site) to the 2nd table (second site) and join them, then transfer the result of join into site 3 Main factors: We have toRead more
Technique 1: Transfer second table (from 2nd site) to 2nd table (first site) and join them, then transfer the result of join into site 3
Technique 2: Transfer 1st table (from 1st site) to the 2nd table (second site) and join them, then transfer the result of join into site 3
Main factors: We have to choose the site and table which contains less data in order to minimize the data transfer cost
See lessHow are joins realized in most NOSQL systems?
Many NOSQL systems do not provide join operations as part of the query language itself ➔ The Joins need to be implemented in the application programs
Many NOSQL systems do not provide join operations as part of the query language itself
➔ The Joins need to be implemented in the application programs
See lessWhat are advantages of Distributes Databases? Give at least three examples and explain them briefly!
• Better representation of organizational structures • Improved shareability and local autonomy • increased availability and reliability (due to replication) • improved performance • Economics - it may cost less to create a network of smaller computers with the power of a single large computer 1. ReRead more
• Better representation of organizational structures
• Improved shareability and local autonomy • increased availability and reliability (due to replication)
• improved performance
• Economics – it may cost less to create a network of smaller computers with the power of a single large computer
1. Reflects organizational structure many organizations are naturally distributed over several locations.
2. Improved shareability and local autonomy The geographical distribution of an organization can be reflected in the distribution of the data; users at one site can access data stored at other sites. Data can be placed at the site close to the users who normally use that data.
3. Improved availability In a centralized DBMS, a computer failure terminates the operations of the DBMS. However, a failure at one site of a DDBMS or a failure of a communication link making some sites inaccessible does not make the entire system inoperable. Distributed DBMSs are designed to continue to function despite such failures.
4. Improved reliability because data may be replicated so that it exists at more than one site, the failure of a node or a communication link does not necessarily make the data inaccessible.
5. Improved performance as the data is located near the site of “greatest demand,” and given the inherent parallelism of distributed DBMSs, speed of database access may be better than that achievable from a remote centralized database.
See lessWhat is consistent Hashing?
Consistent hashing • Special kind of hashing, which minimizes the number of keys that have to be remapped when the size of a hash table is changed • Assumes that the result of the hash function h(key) is an integer value, usually in the range 0 to Hmax = 2n-1, where n is chosen based on the desiredRead more
Consistent hashing
• Special kind of hashing, which minimizes the number of keys that have to be remapped when the size of a hash table is changed
• Assumes that the result of the hash function h(key) is an integer value, usually in the range 0 to Hmax = 2n-1, where n is chosen based on the desired range for the hash values
See lessDifferent Categories of NOSQL Systems?
1. Document stores: •Document-based NOSQL systems store data as collections of similar documents. • Resemble complex objects • Do not require to specify a schema, but are specified as self-describing data • Each document can have different data elements (attributes) • Can be specified in various forRead more
1. Document stores:
•Document-based NOSQL systems store data as collections of similar documents.
• Resemble complex objects
• Do not require to specify a schema, but are specified as self-describing data
• Each document can have different data elements (attributes)
• Can be specified in various formats, such as XML or JSON (JavaScript Object Notation)
• Are accessible via their document id
Examples: Mongo DB
2. Key-value stores:
• Every data item (value) must be associated with a unique key
• Retrieving the value by supplying the key must be very fast
• Value-
1. Can have very different formats for different key-value storage systems:
2. String / array of bytes: the application using the key-value store has to interpret the structure of the data value
3. Structured data rows (tuples) similar to relational data
4. Semi structured data using a self-describing data format
Example: Amazon Dynamo DB, Project Voldemort
3. Wide column stores:
A wide column store is a type of key-value database. It uses tables, rows, and columns, but unlike a relational database, the names and format of the columns can vary from row to row in the same table.
Working Principle-
• Vertical partitioning – tables are partitioned by column into column families
• Each column family is stored in its own files
• Versioning of data values is allowed
• The key is multidimensional (in contrast to key-value stores)
Examples: Google distributed storage system (BigTable), Apache Hbase
4. Graph-Databases:
Data is organized as a graph, which is a collection of nodes, relationships, and properties.
Node-
• Can contain properties
• Can contain labels, which groups nodes with the same label into subsets for querying purposes
Relationship-
• Is directed, each relationship has a start node and an end node
• Can contain properties
• Has a relationship type, which helps to identify similar relationship types for querying purposes
Properties-
Store the data items associated with nodes and relationships as list of key-value pairs
Example: Neo4j
5. Hybrid Systems:
Hybrid SQL‐NoSQL database solutions combine the advantage of being compatible with many SQL applications and providing the scalability of NoSQL ones.
Example: Xeround
See lesswhat is Eventual Consistency?
If no new updates are made to a given data item eventual consistency informally guarantees that eventually all accesses to that item will return the last updated value.
If no new updates are made to a given data item eventual consistency informally guarantees that eventually all accesses to that item will return the last updated value.
See lessCAP Theorem
In a distributed system with data replication only two of the following properties can be guaranteed at the same time: • Consistency: the nodes will have the same copies of a replicated data item visible for various transactions • Availability: each read or write request for a data item will eitherRead more
In a distributed system with data replication only two of the following properties can be guaranteed at the same time:
• Consistency: the nodes will have the same copies of a replicated data item visible for various transactions
• Availability: each read or write request for a data item will either be processed successfully or will receive a message that the operation cannot be completed.
• Partition Tolerance: the system can continue to operate if the network connecting the nodes has a fault that results in two or more partitions, where the nodes in each partition can only communicate among each other
See lessHow is a vertical partitioning of a relation specified? How can a relation be put back together from a complete vertical partitioning?
Vertical partitioning involves creating tables with fewer columns and using additional tables to store the remaining columns. Normalization also involves this splitting of columns across tables, but vertical partitioning goes beyond that and partitions columns even when already normalized. The primaRead more
Vertical partitioning involves creating tables with fewer columns and using additional tables to store the remaining columns. Normalization also involves this splitting of columns across tables, but vertical partitioning goes beyond that and partitions columns even when already normalized.
See lessThe primary key is duplicated to allow the original table to be reconstructed. Using join operation to reconstruct them.
How is a horizontal partitioning of a relation specified? How can a relation be put back together from a complete horizontal partitioning?
Horizontal partitioning divides a table into multiple tables. Each table then contains the same number of columns, but fewer rows. For example, a table that contains 1 billion rows could be partitioned horizontally into 12 tables, with each smaller table representing one month of data for a specificRead more
Horizontal partitioning divides a table into multiple tables. Each table then contains the same number of columns, but fewer rows. For example, a table that contains 1 billion rows could be partitioned horizontally into 12 tables, with each smaller table representing one month of data for a specific year.
The primary key is duplicated to allow the original table to be reconstructed. Using union operation to reconstruct them
See lessWhat are Nest, Unnest, and intersection join operations?
Nest: Creates a set of values from one or more attributes if the values of the remaining attributes are identical. Unnest: Inverse operation Intersection Join: If there is a nonempty intersection set between qualifying attributes, tuples are associated.
Nest:
Creates a set of values from one or more attributes if the values of the remaining attributes are identical.
Unnest:
Inverse operation
Intersection Join:
If there is a nonempty intersection set between qualifying attributes, tuples are associated.
See lesswhat is non first normal form?
The First Normal Form (1NF) is the fundamental requirement for the relational model and states that values of attributes have to be atomic. Simultaneously, 1NF is responsible for several drawbacks of the relational model ➔ an extended data model should not require 1NF. Objects of the Non First NormaRead more
The First Normal Form (1NF) is the fundamental requirement for the relational model and states that values of attributes have to be atomic.
Simultaneously, 1NF is responsible for several drawbacks of the relational model
➔ an extended data model should not require 1NF.
Objects of the Non First Normal Form are defined as follows:
• Every atomic value (such as integer, float, string) is an object.
• If a1, a2, … , an are distinct attribute names and o1, o2, … , on are objects, then (a1:o1, a2:o2, … , an:on) is a tuple object.
• If o1, o2, … , on are objects, then {o1, o2, … , on} is a set object.
Each tuple of a NF2 relation can contain such objects
See lessDiscuss why the weaknesses of the relational data model and relational DBMS may make them unsuitable for advanced database applications?
Poor representation of real-world entities - The process of deriving relations from a conceptual database often leads to the creation of relations that do not directly correspond to modeled entity types. Cause • complex entities consists of other entities • entities are described by multi-valued attRead more
The process of deriving relations from a conceptual database often leads to the creation of relations that do not directly correspond to modeled entity types. Cause • complex entities consists of other entities • entities are described by multi-valued attributes Result • fragmentation of a entity type into many relations • is inefficient and leads to many joins during query processing 2. Semantic Overloading The relational model uses only one construct for representing data and relationships between data: the relation. There is no mechanism to distinguish between entities and relationships, or to distinguish between different kinds of relationship that exist between entities. Often, attributes of different entities are mixed within one relation. Considering only the given relation, we cannot know, which attributes belong to a certain entity or relationship. ➔ the relational model is said to be semantically overloaded 3. Poor support for integrity and general constraints Integrity refers to the validity and consistency of stored data. Integrity is usually expressed in terms of constraints, which are consistency rules that the database is not permitted to violate. Many commercial systems do not fully support these constraints and it is necessary to build them into the applications. This is dangerous and can lead to duplication of effort and inconsistencies. There is no support for general constraints in the relational model, which again means that they have to be built into the DBMS or the application. 4. Homogeneous data structure The relational model assumes both horizontal and vertical homogeneity. • Horizontal homogeneity means that each tuple of a relation must be composed of the same attributes • Vertical homogeneity means that the values in a particular column of a relation must all come from the same domain The first normal form requires that the intersection of a row and column must be an atomic value. Drawbacks of Homogeneity • too restrictive for many (more complex) “real-world” objects • leads to unnatural and inefficient joins. 5. Limited Operations The relational model has only a fixed set of operations, such as set and tuple-oriented operations, operations that are provided in the SQL specification. Since (at least older versions of) SQL is not computationally complete, new operations cannot be specified. This is too restrictive to model the behavior of many real-world objects. 6. Difficulty handling recursive queries Atomicity of data means that repeating groups are not allowed in the relational model. As a result, it is extremely difficult to handle recursive queries, that is, queries about relationships that a relation has with itself (directly or indirectly). 7. Impedance Mismatch Older versions of SQL lack computational completeness and could not be used to develop more complex database applications. To overcome this problem, SQL can be embedded in a procedural programming language. However, this approach produces an impedance mismatch, because different programming paradigms are mixed: • SQL is a declarative language that handles many rows of data at a time • common high-level languages (such as C) are procedural languages that can handle only one row of data at a time Since the type systems are different, type checking is prevented and necessary conversions require a lot of programming effort and runtime resources.
See less